Microsoft Graph Presence Source (Get) Configuration
Introduction
The Microsoft Graph Cloud Communications Presence APIs are used by AnywhereNow for two distinct presence actions, Get Presence states of agents and Set Presence state of agents:
-
This article: Microsoft Graph Presence Source enables the UCC A Unified Contact Center, or UCC, is a queue of interactions (voice, email, IM, etc.) that are handled by Agents. Each UCC has its own settings, IVR menus and Agents. Agents can belong to one or several UCCs and can have multiple skills (competencies). A UCC can be visualized as a contact center “micro service”. Customers can utilize one UCC (e.g. a global helpdesk), a few UCC’s (e.g. for each department or regional office) or hundreds of UCC’s (e.g. for each bed at a hospital). They are interconnected and can all be managed from one central location. to continuously get (collect) presence of Teams users, and
-
See other article: Microsoft Graph Presence Publisher which enables the UCC to set presence of Teams users on-demand by AnywhereNow components.
For more information on the Graph API, see Microsoft’s documentation on https://learn.microsoft.com/en-us/graph/api/resources/presence?view=graph-rest-1.0
Important
While it is technically possible to create one "super" App to control all AnywhereNowGraph API calls to Microsoft 365, we recommend registering the Microsoft Graph Presence Publisher (set) and the Microsoft Presence Source (get) as two separate apps in your Microsoft Entra ID Formerly known as Azure Active Directory (or Azure AD, or AAD).
-
Firstly, either the Presence Publisher app or the Presence Source app , could generate a higher load/volume in the Microsoft Graph API than expected, which could lead to throttling Throttling, in the context of a software cloud delivery service, is the practice of temporarily suspending or diminishing access to a service offering to a cloud customer. Because cloud platforms are mostly multi-tenant, shared platforms and the usage at any moment of many customers is unpredictable, throttling is a normal and logical procedure of retaining a cloud service for all customers, sometimes at the expense of one or a handful of customers who are at that time using too many resources for the backend platform. Not only a customer itself, but also a "noisy neighbour" on the same platform can be the cause of throttling. Usually service will be resumed at a normal level after a short cool-down period, but can even take up to 24 hours or more. In Microsoft 365 throttling is usually indicated by "429 errors" or "server too busy" messages in logfiles or replies. or other issues.
-
Secondly, Publishing other users' Presence with the Publisher app may not be desired or legally permitted in your company, region or country, making this an optional feature.
High Level Steps
In order to start collecting presence for Microsoft Teams users, there are two requirements per tenant:
-
Microsoft Entra ID Formerly known as Azure Active Directory (or Azure AD, or AAD) App Registration:
-
Register an app in Microsoft Entra ID to query the Microsoft Graph APIs.
-
-
Choose Authentication Method:
-
Delegated Permissions:
Authenticate using a user account (username and password).
-
Application Permissions:
Authenticate using a Client ID and Client Secret.
Introduced in DC2024.02
-
Microsoft Entra Id App Registration setup
Tip
As Microsoft enabled throttling to prevent an overload off API calls, it is advised to use a separate Microsoft Entra ID App registration per UCC Service.
In order to prevent throttling, AnywhereNow queries a maximum of 650 users per request. With the limitation of a maximum of 1.500 requests per 30 seconds. This way AnywhereNow is able to collect presence of 15.000 uniquely configured Agents per App registration.
Please find below the steps to setup an App Registration in Azure.
- Navigate to: https://entra.microsoft.com/
-
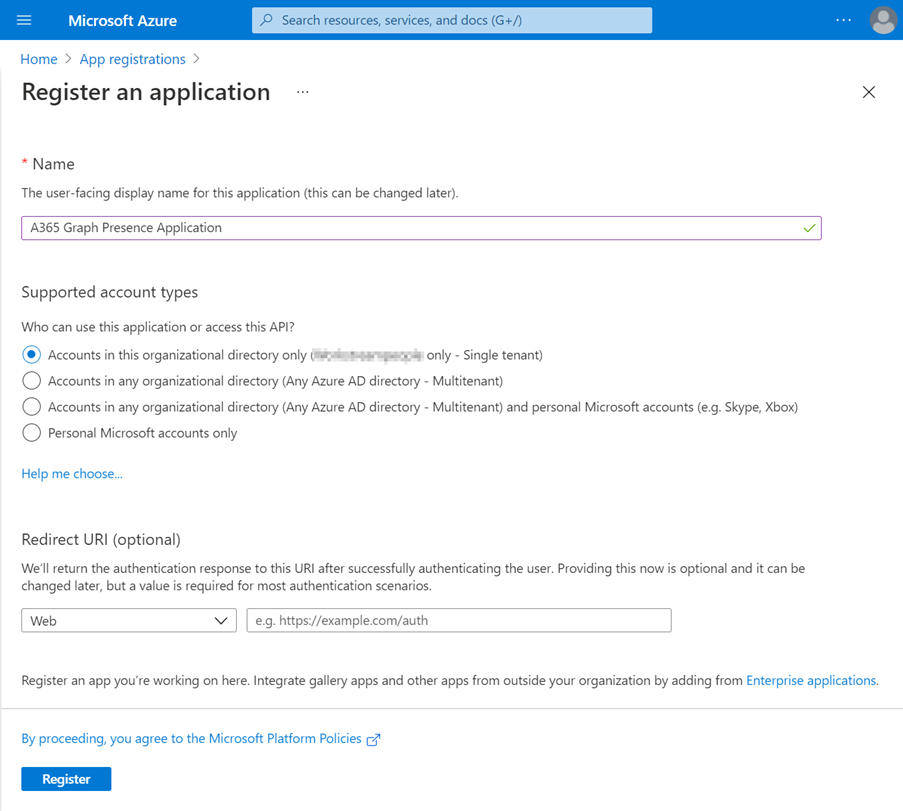
Under Applications -> App registrations create a new App registration
-
Provide a Name for the application, for example: AnywhereNow Graph Get Presence Application
-
Select the account type Single tenant only
-
Click “Register”
-
-
On the API permissions tab,
- Delegated Permissions
- Application Permissions
Add the following Delegated Microsoft Graph permissions:
 User.ReadBasic.All - Read all users' basic profiles
User.ReadBasic.All - Read all users' basic profiles
Description: Allows the app to read a basic set of profile properties of other users in your organization on your behalf. Includes display name, first and last name, email address and photo.
Why is this required? To allow the Graph Presence Source to translate UPN In Windows Active Directory, a User Principal Name (UPN) is the name of a system user in an email address 'like' format. A UPN (for example: john.doe@domain.com) consists of the user name (logon name), separator (the @ symbol), and domain name (UPN suffix). to ID, ID is required to retrieve presence from user.
Permission name: Microsoft Graph / User.ReadBasic.All
 Directory.Read.All - Read directory data
Directory.Read.All - Read directory data
Description: Allows the app to read data in your organization's directory.
Why is this required? To allow the Graph Presence Source to cache user details (display name, sip address, id, UPN) from all employees, in order to minimize the number of request to graph.
Permission name: Microsoft Graph / Directory.Read.All
 Presence.Read.All - Read presence information of all users in your organization
Presence.Read.All - Read presence information of all users in your organization
Description: Allows the app to read presence information of all users in the directory on your behalf. Presence information includes activity, availability, status note, calendar out-of-office message, timezone and location.
Why is this required? To allow the Graph Presence Source to retrieve current presence from users utilizing a single service account.
Permission name: Microsoft Graph / Presence.Read.All
Introduced in DC2024.02
Add the following Application Microsoft Graph permissions:
 Presence.Read.All - Read presence information of all users in your organization
Presence.Read.All - Read presence information of all users in your organization
Description: Allows the app to read presence information of all users in the directory without a signed-in user. Presence information includes activity, availability, status note, calendar out-of-office message, timezone and location.
Why is this required? To allow the Graph Presence Source to retrieve current presence from users.
Permission name: Microsoft Graph / Presence.Read.All
 Domain.Read.All - Read domains
Domain.Read.All - Read domains
Description: Allows the app to read all domain properties without a signed-in user.
Why is this required? To allow the Graph Presence Source to retrieve the domains from the tenant.
Permission name: Microsoft Graph / Domain.Read.All
 User.Read.All - Read all users' full profiles
User.Read.All - Read all users' full profiles
Description: Allows the app to read user profiles without a signed in user.
Why is this required? To allow the Graph Presence Source to translate UPN to ID, ID is required to retrieve presence from user.
Permission name: Microsoft Graph / User.Read.All
-
Since the Admin consent are required, click the button “Grant admin consent for <tenant>”.
Note
Only a tenant administrator can grant the admin consent
-
On the Authentication tab, change “Allow public client flows” to “Yes”.
-
Click “Save”
Note:
This is a setting mainly required for Delegated authentication permissions method. If all your Graph Presence services are setup for Application authentication permissions this op is not required.
 Read more
Read more
Why Allow public client flows is required: This setting enables the app to authenticate as a public client using delegated permissions. It allows AnywhereNow to retrieve presence data via Microsoft Graph without storing a client secret, using secure token flows like OAuth 2.0 with PKCE. This is essential for service accounts configured per tenant.
-
-
On the Overview tab, copy both the Application (client) ID and the Directory (tenant) ID
-
These IDs need to be used for Configure the Presence Source.
-
Authentication Methods
- Delegated Permissions
- Application Permissions
User Account
Note
You will need one user account for each tenant.
Note
Account should be cloud only and not federated When using AnywhereNow in combination with Federation you can add agents working with a Skype for Business or Teams account to your UCC. with an on premise ADFS.
The user account that is used to retrieve presence must be a Microsoft Entra ID Useraccount. This useraccount has the default ability to retrieve presence of other users in the same tenant.
The account does not require any permissions, nor does it need any licenses. Simply create an new user account without any licenses to use it like a service account.
Note
During the setup procedure, the account requires access to Teams to read the presence and complete the setup.
-
This username and password need to be used for Configure the Presence Source.
Password policy
-
Make sure that the password never expires.
-
Please change the password from the standard password by logging in with this account and change the password.
-
Make sure that the password isn't changed while in use by MS Graph Presence Provider.
-
Make sure to use a long and safe password.
Note
When creating a login or a password make sure it does NOT contain the following characters: "", `, %, or whitespace
-
It is required to disable MFA for the useraccount, to prevent human intervention when the user token expires.
Note
For disabling MFA on a single useraccount please see latest Microsoft guidelines using exclusions on Conditional Access Policies like:
Manage users excluded from Conditional Access policies - Microsoft Entra ID Governance | Microsoft Learn.For more in-depth explanations by Microsoft see Enable Microsoft Entra multifactor authentication - Microsoft Entra ID and subsequent excluding the users for your policy Block access for users with elevated insider risk - Microsoft Entra ID | Microsoft Learn
-
If the password is changed for some reason it always requires human intervention.
-
Client Secret
Introduced in DC2024.02
An App authenticated with a ClientId and ClientSecret is used to get presence via the Graph API. The ClientSecret needs to be created separately (and periodically renewed) on the Entra ID App registration.
- Navigate to the Application you created in Microsoft Entra Id App Registration setup
-
On the Client secret tab, click on New client secret:
-
Enter a Description and set the Expires value
-
On the next screen, copy the Value of this secret (so not the Secret ID)
-
The Value needs to be used for Configure the Presence Source.
-
Configure Agents for presence collection via MS Graph
In order to collect presence for Agents using Microsoft Graph, make sure that the UPN field in the SharePoint Agent list is populated with the correct UPN of the Agent.
Configure the Presence Source
- Delegated Permissions
- Application Permissions
In the config.xml of the UCC service, add the following configuration as child node to the <PresenceProvider> element. Make sure to enter a unique ID (we recommend the domain name). Set the TenantId and ClientId copied during Microsoft Entra Id App Registration setup.
<MsGraphPresenceSource enabled="true">
<Accounts>
<Account Id="my-presence-account1" ClientId="xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx" TenantId="xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx" />
</Accounts>
</MsGraphPresenceSource>This will enable the MsGraphPresenceSource inside the UCC. However after starting the UCC the provider is not authenticated to retrieve presence. Open the UCC logs and search for the following line:
MsGraphPresenceSource GraphPresenceManager::Graph API needs authentication for account with ID 'my-presence-account1' (tenant: xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx). Please login on the following wAdditional Information
Multiple tenants
It is also possible to use multiple tenants. For example given there is an Azure tenant A dedicated and trusted instance of Azure AD. The tenant is automatically created when your organization signs up for a Microsoft cloud service subscription, such as Microsoft 365. An Azure tenant represents a single organization. [Taken from Microsoft Docs] with 10 users and another Azure tenant with 25 users. Both tenants have to be added in the config as an Account. Always make sure to login with a user from the same tenant.
UCC cache policy
When the complete cache of a UCC is removed, the tokens of the account will also be removed and a new device token must be granted access to start collecting presence information again. This can be prevented by not removed the following folder:
In the config.xml of the UCC service, add the following configuration as child node to the <PresenceProvider> element. Make sure to enter a unique ID (we recommend the domain name). Set the TenantId and ClientId copied during Microsoft Entra Id App Registration setup.
Note
EncryptedSecret: Encrypted secret of the Azure application. Encrypt with A365.PWTool.exe located in UCC install package
<MsGraphPresenceSource enabled="true">
<Accounts>
<Account Id="my-presence-account1" ClientId="xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx" TenantId="xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx" EncryptedSecret="xxxx"/ />
</Accounts>
</MsGraphPresenceSource>